Anyone who has worked in healthcare knows how challenging it can be to defend against cyberattacks. Most hospitals, clinics and health systems face the same possible vulnerabilities as any other enterprise business impacting their computers, laptops, communications infrastructure and mobile devices. But they also must support a whole host of sensors, scanners and medical equipment that is unique in healthcare — and that is increasingly vulnerable to advanced attackers. Compounding matters, many medical devices were never built with security in mind, haven’t been updated in years and most likely cannot support native cybersecurity.
It’s clear that specialized healthcare environments require specialized security solutions, and Ordr Clinical Defender 8.1 serves that need. The platform is designed to integrate into a healthcare environment. It uses passive scanning to do all of its work so as not to interfere with critical healthcare-related communications, and it does not have to deploy any software agents. Instead, it can collect all of the data it needs using virtual or hardware-based sensors, application programming interface integrations, NetFlow or its own Ordr Software Inventory Collector.
Click the banner below to dive deeper into zero trust and its benefits for healthcare.
Clinical Defender Provides Much-Needed Clarity
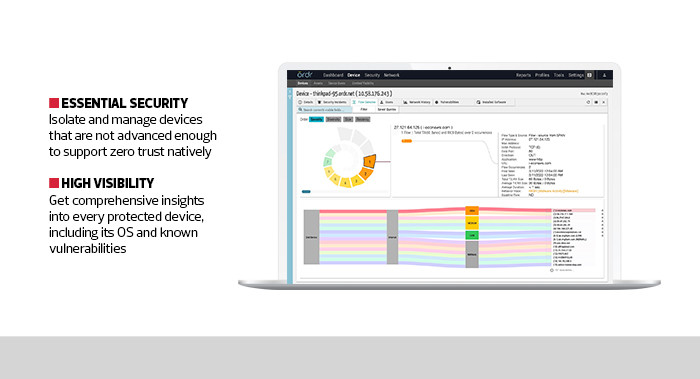
The information Clinical Defender gathers is impressive and provides a deeply granular map of everything operating within a healthcare network, from typical computers to highly specialized medical devices and Internet of Things sensors.
Devices can be sorted based on type, location, function, priority or almost anything else. And users get to see a lot of information about each device, including what operating system it’s running, its connection status, what it communicates with, where it’s located and any known vulnerabilities, such as a weak default password.
In addition, devices can be checked against an organization’s computerized maintenance management system to ensure that the right device is installed and that nothing is missing.
Clinical Defender insights can be invaluable in budgetary planning, providing evidence about future needs and requirements. The insights could also help to justify spending where it would most improve operations or patient care while avoiding wasting money on things that don’t contribute much to operational efficiency.
Secure Healthcare’s Complex Environment
Clinical Defender can be used to prioritize fixing vulnerabilities based on factors such as whether a device is used to sustain life or treat patients, the problem’s severity, its location and other factors. Once a fix is made, the platform will check to ensure that it worked, and that it never reverts back to a vulnerable state.
If inventory and vulnerability management was all that Ordr Clinical Defender 8.1 did, it would still be incredibly useful in healthcare, but it also does so much more. In fact, it can act as the cornerstone for all cybersecurity activities.
For example, one big problem in healthcare is that Internet of Medical Things devices are often designed with a single purpose, such as initiating a medical scan or monitoring a patient’s vitals, to the point that there is no overhead to add cybersecurity. This makes them extremely difficult to protect from clever attackers looking for a way into a hospital network. Clinical Defender can help by isolating the devices and building zero-trust policies around them, effectively bringing them into a zero-trust environment.
Trying to protect a healthcare environment using tools designed for other businesses adds extra work and complexity for already overworked IT staff. Instead, hospitals and other healthcare organizations should invest in a platform such as Ordr Clinical Defender 8.1, which is specifically designed for their needs and their unique ecosystem.
LEARN MORE: How to mitigate risk for healthcare in an increasingly connected environment.
SPECIFICATIONS
Product Type: Asset tracking, vulnerability management and protection platform
Continuous Defense: Monitors for attack tools within an environment, suspicious communications, lateral movement and beaconing behaviors to detect ongoing attacks
Deep Protection: Monitors all device communications, including those within subnets and virtual local area networks
Defense in Depth: Can segment network devices and immediately respond to possible attacks, limiting the effectiveness of anything that manages to slip through
Post-Attack Updates: Can automatically update policies and playbooks after an attack to prevent future incursions