At the core of Cisco Duo’s MFA capabilities is the requirement that users provide two or more verification methods before they can access sensitive information or applications.
For health systems, where multiple professionals access various systems and data daily, using Duo addresses a number of potential attack vectors and mitigates the risks associated with unauthorized access.
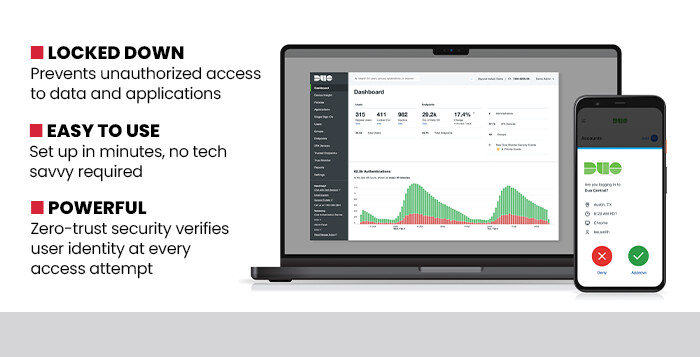
Using a zero-trust security model, Duo verifies user identity during every attempt to access network resources, helping protect hospitals and clinics from identity-related security breaches. By using push notifications to mobile devices to verify users, organizations boost their cybersecurity posture against common threats such as phishing, ransomware and theft.
READ MORE: IAM addresses the challenges of increasingly complex IT environments.
Cisco Due Integrates With Existing Systems
On a trip to a conference in Las Vegas, I used Duo and was impressed by two additional features:
Integration with Existing Systems
As an IT administrator, the worst thing that I ever had to manage was integrating new solutions into an existing ecosystem of applications and tools. Implementing new security measures in particular is daunting, to say the least. What’s great about Cisco Duo is its seamless integration with thousands of applications and services commonly used in a number of industries. From cloud storage solutions to administrative software, payroll and back-end systems, Duo enhances security without disrupting current workflows or protocols.
EXPLORE: This is the key step beyond authentication in identity and access management.
Simplicity at Its Best
It took just minutes to get secure access to resources. For healthcare systems, this easy setup minimizes disruption while maximizing effectiveness. The key to this is Cisco Duo’s intuitive interface, which pares down the steps needed to complete the authentication process. For example, upon setting up Duo for the first time, users are asked to choose either a passkey or the Duo mobile app. I timed each one, using both at home and while traveling from Las Vegas to San Francisco for work. At no point in my journey did I experience an issue with either method. Each takes about the same time to set up (about two minutes). Within eight minutes, I was fully set up in the system through both methods of identification. More important, resetting the system was easy to do as well, and didn’t require an IT administrator’s intervention.