Martin Littmann, CTO and CISO, Kelsey-Seybold Clinic, emphasizes the importance of a holistic approach to data storage throughout an organization's IT environment. Photography by Phoebe Rourke
They also managed to restore individual files from backups so everyone could continue to work. By the end of the day, they had everything running again, almost as if the event had never happened. “We survived, but it did lead us to change the way we approached data protection moving forward,” Littmann says.
Littmann’s team relies on both on-premises and cloud-based storage, and has used a range of storage products from different vendors over the years. Currently, Kelsey-Seybold works with NetApp and Pure Storage for file storage and block storage, respectively.
RELATED: Discover 7 email security strategies to keep patient data safe from evolving cyberattacks.
“From a storage perspective, we’ve always tried to stay with leading-edge, top-tier enterprise solutions,” Littmann says. His team turned to Pure Storage FlashArray, in large part because it supports the organization’s Epic electronic medical records system as well as its virtual desktops.
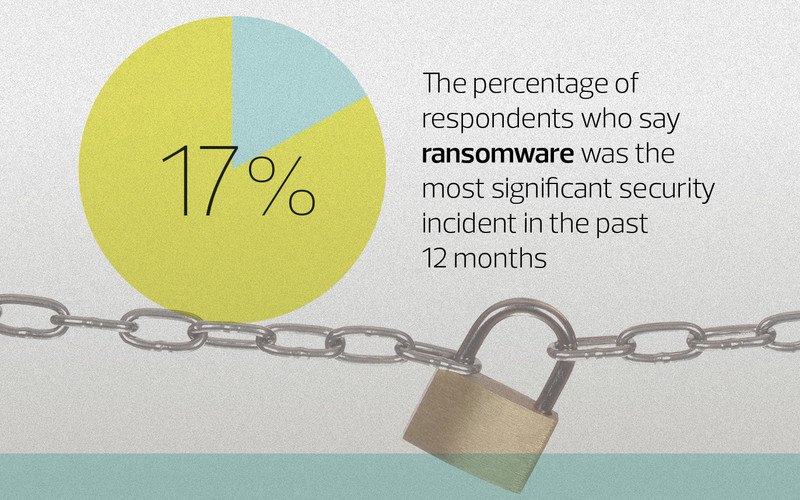
One big difference today is the use of immutable backups, which the team creates with a Pure tool called SafeMode. But most important, Littmann says, is the focus now on protecting the network and endpoints — the weak spots that hackers usually like to target.
“Protecting your data is not just about the quality of your storage systems or how you handle backups and recovery,” Littmann says. “It’s everything you do across your organization; it’s how you manage your house.”
Click the banner below to discover healthcare-related security best practices and tips.