Google Threat Intelligence Offers Much-Needed Insights
At the heart of the platform, Google Threat Intelligence uses four key elements to keep track of global threats. First is the Mandiant Intel Grid, which was recently purchased by Google. That real-time network consists of more than 4 million guest instances set in over 100 countries. Those instances are attacked thousands of times every hour. Additionally, attack information gathered from Gmail and Google Chrome, plus everything submitted through VirusTotal, is added to the tracker. That makes for possibly the world’s biggest network for captured threat intelligence.
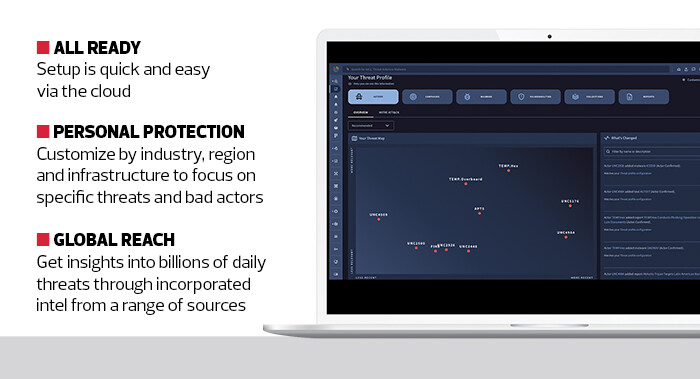
All of that raw intelligence would easily overwhelm almost any security team. Thankfully, Google Threat Intelligence lets users personalize their feeds and power their dashboards based on industry, location and other factors. For example, in testing, I set up my feed as if I were a healthcare facility operating in the U.S. That gave me a wealth of intelligence about threat actors, active campaigns and tactics being used by real adversaries trying to disrupt healthcare operations.
A Powerful Platform to Bolster Healthcare Security
The threat intelligence can be further customized to include all of the public-facing assets at a healthcare facility so that active campaigns can be quickly and easily matched with existing infrastructure and security. For example, I could easily see if my test hospital had any infrastructure that was being targeted by active threats aimed at healthcare in my area, discover how those bad actors implemented attacks in other places, and learn how to inoculate and monitor my systems against any similar attacks.
The security landscape for providers will only become more challenging, but knowing your enemy is half the battle. Google Threat Intelligence will ensure that no healthcare facility is caught by surprise when attacked. Instead, malicious actors will find a well-informed and properly designed defense ready to protect this critical industry.
SPECIFICATIONS
PRODUCT TYPE: Cloud-based threat intelligence platform
DEPLOYMENT: Software as a Service
CAPABILITIES: Personalized threat intelligence, attack surface management, post-breach analysis tools
THREAT INTEL SOURCES: Chrome Safe Browsing, VirusTotal, Mandiant Threat Intelligence, Gmail (phishing)
ADDITIONAL FEATURES: Dark web and website spoof monitoring