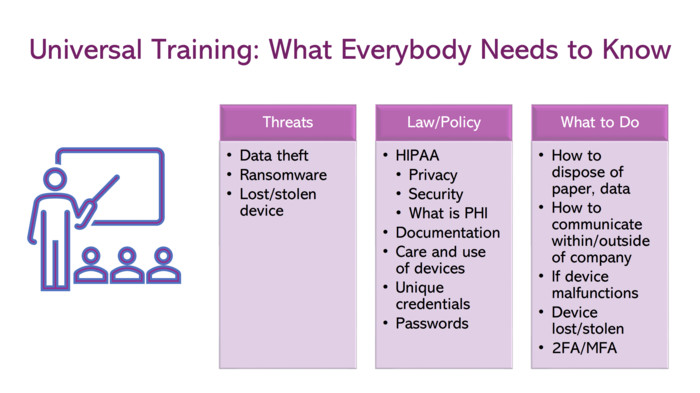
Why Employee Training Is Key for Stronger Security
Healthcare organizations, including aging-services providers, handle a lot of valuable data that cybercriminals would like to access.
“We know that there are people out there trying to get our data and developing ways to break into our systems,” Gray said. “You can have the best security system, but if you leave the door unlocked, someone can just walk in. Oftentimes, our defenses are pointed outward, and we're not looking inward.”
He stressed the importance of developing a strong employee training program to improve an organization’s cybersecurity posture, especially as business email compromise and ransomware remain top threats. It only takes one careless moment or mistake for malicious actors to gain access.
Phishing techniques are becoming more sophisticated as cybercriminals conduct detailed research on employees outside an organization’s C-suite, Gray added. The use of artificial intelligence–powered tools to better target phishing attempts is a growing concern.
And previous ransomware victims run the risk of becoming repeat targets, he said, because malicious actors have already identified their weak defenses.
What are the top #security issues senior care organizations should focus on for 2024? @ElizaJennings leaders share their #HealthIT insights at #LeadingAge23: pic.twitter.com/Mi7UvDtDu1
— HealthTech Magazine is 🔜 to #LeadingAge23 (@HealthTechMag) November 7, 2023
That’s why conducting regular security risk assessments is a major step toward better security, Griveas said.
“A good security risk analysis isn't supertechnical,” she added. “It really is, do we know what we have? We need a device inventory. We know what's out there. We know what our policies are. Do we have encryption to protect our devices, our email communication? Getting your mind around that and understanding what you have is superimportant to be able to lay the foundation to actually train people.”
Having an extensive understanding of your environment is necessary, Griveas said, because organizations should operate on a “when, not if” assumption about the potential for cyberattacks.
“One of the elements that is just critical to training — especially leadership, governing bodies — is understanding what our obligations are under the law as it pertains to our technology and mitigating the risks; but also, how we can use good cyber hygiene to provide ourselves defenses if things do go wrong,” Griveas said.
She also stressed the importance of having a compliance program, which long-term care may not be as diligent about compared with other healthcare organizations.