Healthcare cybercrime is on the rise. Federal records show that 510 major data breaches were reported last year, with each involving 500 or more records. That’s a 37 percent increase over 2018.
It isn’t the only spike: With the exception of 2015, data breaches of this magnitude have increased annually since the Department of Health and Human Services’ Office for Civil Rights began publishing figures in 2009.
The total number of breached records rose from 13,947,909 two years ago to 41,335,889 in 2019, with the recent figure representing 12 percent of the U.S. population.
Meanwhile, medical records are selling for up to $1,000 online, and efforts to repair the damage from the loss of personal information can be costly and time-consuming.
Still, some organizations may struggle with knowing how and where to take action. Consider adopting the following strategies to help identify your weakest links and to better protect your organization’s network — and those who use it.
1. Start with a Cybersecurity Assessment of the Network
Achieving HIPAA compliance is often seen as a marker that personal information is protected. The industry is myopic in terms of this idea, said Mikela Lea, principal field solution architect for CDW, and organizations don’t always take the time to examine the vulnerabilities of their infrastructure.
That’s why insights from an external party are crucial. Speaking earlier this month at a CDW Bring IT On session — held virtually due to the cancellation of the HIMSS20 conference in Orlando, Fla. — Lea explained that third-party security assessments help organizations identify weak points in their networks.
They can also be useful as systems evaluate needs after a merger or acquisition. New homeowners, Lea noted, wouldn’t start out by replacing the roof, plumbing or wiring without evaluating the current state of each one.
“So, why do we treat our networks that way?” Lea said. “Why do we go into an environment and immediately put on the new roof, the new air conditioning, continue to put on all the latest and greatest without ever having someone to come in and make sure that we know where our weaknesses are?”
In leveraging the Cybersecurity Framework from the National Institute of Standards and Technology, she explained, security assessments can identify problems and network visibility to aid in effectively planning and prioritizing security strategies going forward.
“Really looking at the overall environment and making sure that we’re securing all of the different layers of that environment is going to make a major difference with what we’re trying to do,” said Lea.
INSIDER EXCLUSIVE: Become a HealthTech Insider to watch the entire Bring IT On webinar.
2. Make the Effort to Secure All Medical Devices
There’s no doubt that medical device security is a priority for healthcare organizations, but Lea said she often notices vulnerable devices on networks during her assessments — a problem that can have far greater implications than possible identity theft.
“We’re not only talking about sensitive patient information being leaked out,” May Wang, senior distinguished engineer at Palo Alto Networks, tells HealthTech. “If these devices are compromised, it will be a matter of life and death.”
The greatest security problems associated with these devices go beyond unchanged passwords and outdated software, Wang says. Organizational challenges around device ownership often exist, making it difficult to know who’s using a particular tool and taking the steps to protect it.
“For traditional IT devices, you have the IT network,” says Wang. “But with medical devices, they’re relevant to everyone and every age group.”
To combat this issue and enhance device security, Wang recommends that IT teams focus on three tactics, starting with visibility.
“Healthcare organizations, hospitals — they need to know what is on their networks,” says Wang. “They need an intelligent, automatic tool that tells them how many devices and what devices are on their networks.”
Once a team gains that understanding, she suggests actively monitoring and segmenting medical devices onto their own private networks. This can help organizations to be better prepared for a cyber event and contain any lateral movements attempted by a hacker.
READ MORE: Medical Internet of Things devices are vulnerable to attack. Are yours protected?
3. Don’t Forget to Educate and Train Clinical Staff
On average, targeted healthcare companies each received about 43 impostor emails in the first quarter of 2019 — nearly triple the amount seen in the same quarter in 2018, according to a recent report from enterprise security company Proofpoint.
Perhaps more surprising: Doctors, physicians and administrative staff all ranked as higher targets for attackers than executives and other high-ranking employees.
“If you’re looking at ways to stem cybersecurity,” says Ryan Witt, healthcare industry practice leader at Proofpoint, “then you need to start with identifying those attacks.”
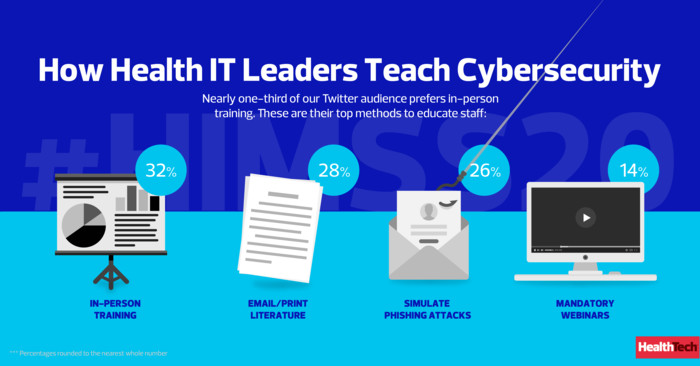
A recent poll of our @HealthTechMag Twitter audience demonstrates how some health IT leaders are educating their staff on cybersecurity.
Today’s attacks target people, not just technology. And today’s hackers, Witt says, have learned to exploit the human factor: workers’ time constraints, curiosity and a natural desire to serve others (a malicious email offering information on how to contain a flu outbreak in the form of a Microsoft Word document, for example).
To make matters worse, a 2019 report from Kaspersky shows that 1 in 4 healthcare workers have never received cybersecurity training.
Educating all staff on the value of security in a clinical setting is critical, Witt says. Deploying tabletop exercises with a focus on real-life consequences can help ensure the message sticks across your entire organization.
“Attitudes of clinicians have reversed when it comes to embracing new technology and security,” says Witt. “The community is embracing the protection of data as a component of the overall wellness program.”
Keep this page bookmarked for our ongoing virtual coverage of HIMSS20. Follow us on Twitter at @HealthTechMag and join the conversation using the hashtags #VirtualHIMSS20 and #CDWHIMSS.