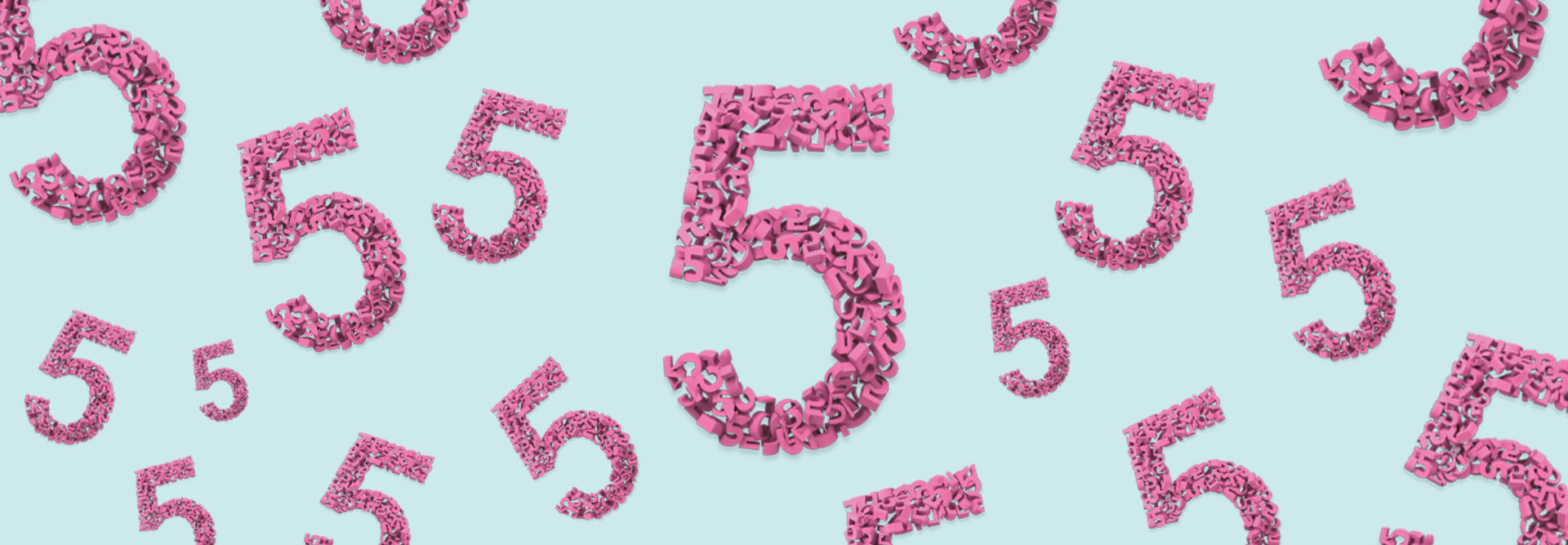2. How Do Identity and Network Segmentation Differ?
Network segmentation covers network connections and zones. Identity segmentation covers user identities, attack path visibility, authentication footprint, behaviors and risk.
3. How Does Identity Segmentation Fit into Zero-Trust Security?
The first steps in zero-trust network access are to define the user identity, establish policies based on the principle of least privilege and verify user device integrity.
Identity segmentation involves monitoring exactly who is accessing what on the IT network and determining which device performed which action.
Zero-trust security enforces continuous validation and authentication before accessing each resource, based on individual identities and devices.
DIVE DEEPER: How does identity segmentation fit into healthcare’s cybersecurity approach?
4. What Are Some Identity Segmentation Challenges in Healthcare?
About 96 percent of healthcare providers use temporary staff each year, according to a 2021 survey. A failure to provision, transition and decommission these user accounts increases identity risk. What’s more, healthcare providers have strict regulations around patient data under federal law. Legacy electronic health records also impede modernization: They can be difficult to integrate with identity providers to facilitate single sign-on, a core element of zero trust.
5. What Other Segmentation Strategies Exist?
Hypervisor segmentation uses overlay networks created by hypervisors to microsegment virtualized IT activities. Agent-based segmentation happens when a software agent is installed to monitor workload identities and attributes and enforce granular isolation per host or container. Hybrid segmentation could be a combination of hypervisor, agent- and network-based segmentation used simultaneously.
UP NEXT: Why should healthcare organizations begin their zero-trust implementations with identity?