8 Steps to a Secure Medical Device Deployment
One of the greatest trends in healthcare through the past several years has been the use of connected devices to provide up-to-the-minute information to providers about patients’ conditions. Continued emphasis on reducing patients’ length of stay, cutting costs and improving care drives rapid adoption of such tools, but not without risk.
Our industry has been beset by several security threats in the past year that directly impact adoption of those devices. Ransomware has become incredibly prevalent and effective at disrupting hospital and patient care operations, and everyone — smaller practices to large academic health systems — has become a victim.
The Mirai botnet, which primarily affected security cameras and other internet-connected devices running the Linux operating system, was devastatingly effective, as it showed how large numbers of compromised machines could be used to disrupt traffic across the internet, including a 1-terabit-per-second distributed denial of service attack against a French web host. Many of those devices had just been installed and did not receive security patches for many Linux kernel or application vulnerabilities.
A number of Android-based botnets have been discovered over the past year as well. These botnets take advantage of compromised smartphones and tablets to deliver malware and DDoS attacks. Since Android devices generally do not receive security patches as frequently as desktops, they are an easy group to target.
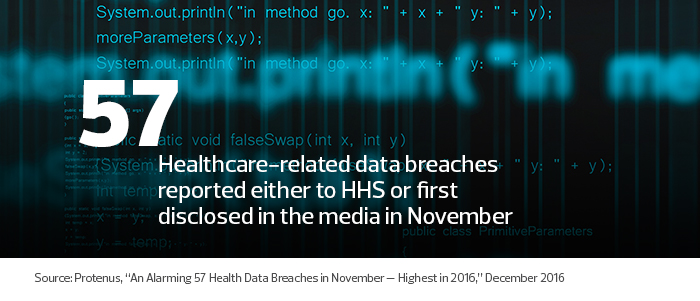
The number of healthcare-related data breaches in 2016 increased sharply in the second half of the year. The first half of 2016 saw a monthly average of 25.3 breaches reported to the Department of Health and Human Services or disclosed in the media, according to the Protenus Breach Barometer report for November.
That number more than doubled in November, when 57 breaches were reported. Such statistics give organizations pause when deciding whether to deploy connected devices.
What should be the best approach to implement connected devices while reducing organizational risk and still delivering improved care? Here are eight steps to consider.
1. Have a Comprehensive Vendor Review or Contract Management Program in Place
Any effort should address the vendors’ risk management program, vendor vulnerability management and disclosure, and support of any underlying operating systems or applications. That allows organizations to make a decision up front whether to use these connected devices to handle information. If a device does not receive security updates or a vendor is not responsive to disclosed vulnerabilities, it’s better to know this before proceeding.
2. Reduce the Amount of Data on Any Connected Device to the Absolute Minimum Necessary
Make sure to keep only what is absolutely necessary on the device. A corollary to this: Keep the services and connectivity of the device to an absolute minimum, and use firewalls and other network-based protection as necessary and appropriate on end-user devices.
3. Create a Separate and Secure Technology Infrastructure for Data Integration
What’s more, constantly update the infrastructure, monitor for vulnerabilities at all levels (operating system, database, application, supporting libraries, code and interfaces) and review for any anomalies in data or system activity. Put all incoming data through a well-tested supporting infrastructure first to reduce risk to your electronic medical record system.
4. Build an Educational Plan Around the Devices for Your Organization and Customers
Ensure that anyone who deploys the devices can understand them, answer potential questions and work with consumers to update and monitor usage. Also, confirm contact information in case of an issue to reduce triage time.
5. Develop a Comprehensive Activity Review Process
Review your users’ device activity on a regular basis, ensuring periodic updates to such tools and resolutions to known vulnerabilities for customers. Such a process must extend to administrators, superusers and anyone else who has access to system data, as insider threats cause many data breaches.
6. Make Sure There's Budget Set Aside
Build in enough budget to ensure the availability of staff to answer customer questions, review devices and infrastructure, and continually assess risk from inside and outside threat vectors.
7. Develop a Staffing Plan
Adequately staff for device deployment, customer service and activity review on the secured infrastructure and devices, and update both regularly. Many vendors claim that their tools require less maintenance or tout the ability to maintain thousands of devices without dedicating full-time staff; that simply is not true for devices containing protected health information, as the HIPAA Security Rule requires regular review of user activity on systems containing PHI.
8. Ensure Your Security and Risk Management Plan Addresses Potential Use Issues
The plan must start with an initially secure configuration of the devices and infrastructure at the device, application, network and infrastructure layers. It then should address how the devices will be kept in a secure state through effective management, review, testing and change management. It must address communication and deployment plans for security vulnerabilities on the device, and how any issues will be mitigated. The plan should take into account the potential that there will be a breach or similar event that will cause the device to not function correctly, and must include annual risk assessments of the entire infrastructure, not just the devices themselves. Pay close attention to account supporting processes, staffing, training and technology.
Hospital technology leaders must approach successful deployment of connected medical devices as a program, not simply a project. Doing so will enable organizations to better mitigate risk by addressing the key issues at multiple levels while still issuing devices that meet immediate needs.









